Comprehensive Guide to Penetration Tests | Tools, Process & Methods
We’re a hub for tech professionals looking to advance & optimize their IT Infrastructure by finding the perfect product, tool, or role. Learn more about us. If you don’t see a product you are looking for on our website you can send us feedback 🙂

Penetration testing is the process of simulating real attacks on a target to assess the risk associated with potential security breaches. This type of simulated environment allows the person performing the assessment to not only discover vulnerabilities but also exploit them where possible.
Penetration tests, also known as pentest are crucial to organizations because they will provide valuable feedback in terms of where they stand from a security point of view. The whole point of security is to minimize the level of threat as much as possible, whether it be digital or physical. No organization can be 100% secure if it has functionality, which is why minimizing the threat landscape is just as important as running the business.
The scope of penetration tests will vary from company to company due to the reason that every organization is different. Some organizations might have excellent security while others might be vulnerable to a variety of exploits.
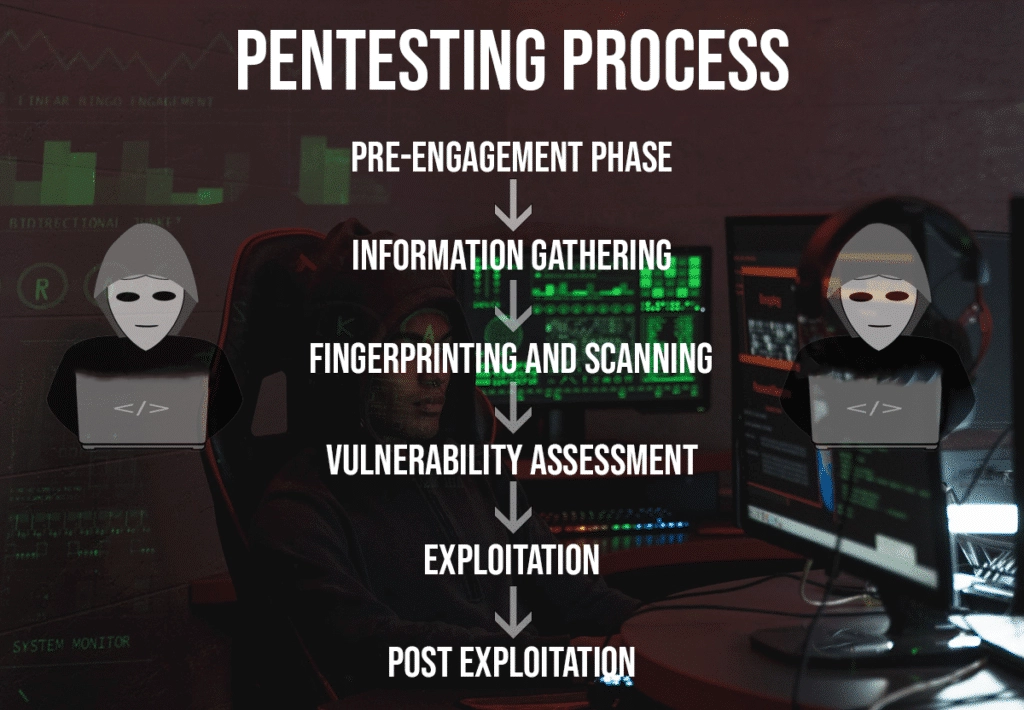
Pre-engagement Phase
BOTTOM LINE UP FRONT: What can be touched/ in scope/ out of scope/ time of day/legal
The first step in a penetration test begins with the pre-engagement phase. This is where you speak with the client to have a better understanding about their goals for the pentest and have a clear understanding of your customer’s objectives. The reason this is very crucial is because it will allow you to specifically tailor the legal forms for each client. All legal forms created should not be the same for each client. Every client has specific needs, which should be clearly laid out in the contract.

Miscommunication with the client is a pentesters worst enemy. Something as simple as the client only wanting a vulnerability scan could be miscommunicated by you performing exploits on those vulnerabilities and end up bringing down a server. It is best practice to never assume clients know security and to clearly explain different concepts so both parties are on the same page.
Before proceeding straight to the scope of work, building a relationship with a client is crucial so trust is created on both ends. In your point of view, you are conducting a penetration test, whether it be physical or digital. In the point of view of the client, they might have a different perspective.
Ask questions such as:
- Is this the first penetration test on the organization?
- If this is the first penetration test, what prompted them to reach out for one?
- What is the type of assessment? Is this penetration test just to check a box for compliance or are they really looking for a deep dive in the assessment on specific assets?
- What exposures are they most worried about?
- Specifically with the CIA Triad, what part of their business are they most worried about being exposed in? Confidentiality? Integrity? Availability?
- Are there any specific assets that are fragile in terms of being taken offline due to the pentest?
Since all companies are different, there are many different questions that should be asked to the client to better understand the scope of work. Be creative when asking questions. Make the client feel secure in terms of laying a good foundation for both parties to start in.
Scope
The scope of a penetration test outlines the objectives the business is looking to complete. These requirements will vary from company to company depending on their size and budget. The main objectives to outline with the scope include:
- Testing requirements
- Target selection
- Scheduling and timeline
- Strategy for testing (black box, gray box, white box)
Here you will identify which IP addresses or hosts (web, network, mobile, wireless, physical) are in scope and which ones should not be touched. For the targets in scope, do they just want vulnerabilities or can exploits be used? Can social engineering be used? What is the testing window for the assessment? Day hours, night hours, or weekend hours? Essentially, you are also creating a “get out of jail free” card. The more information written on the legal forms, the better you are off in terms of legal liability.
Type of Assessment
Since a penetration test can vary greatly in terms of time, it is crucial to understand where your client is looking to have the most impact. It would be a perfect world if organizations had an unlimited budget to perform many assessments but that is just not the case. To better understand, improve their security posture, and be a business enabler, knowing which type of assessment is key:
- Objective based assessment
- Compliance based assessment
- Red team assessment
Objective Based Assessment
Are there specific IPs or hosts that need the most attention? Are they looking to see if databases can be breached? Can administrative (privledged) access be obtained?
Compliance Based Assessment
Compliance based assessment audit an organizations ability to follow and implement a specific set of standards in their environment. Examples include: PCI, HIPPA, FISMA.
Red Team Assessment
Similar to an objective based assessment, the red team assessment will simulate how well an organization’s security posture stands up to attacks from threat actors in a real world environment. It is more stealth and includes a hybrid of attacks such as combining network pentesting with social engineering. One of the main goals of a red team assessment is to test the time it takes for the organization to detect and respond to such attacks while modeling the resiliency against those threats.
Information Gathering
Bottom Line Up Front: Passive reconnaissance
The information gathering phase is all about analyzing publicly available sources of information. I will refrain from saying free public resources because some tools offer ‘freemium’ services, such as being free up until a certain point. Information gathering can be completely done with free tools but if you want to dive deep in your target, the paid sources offer the best bang for your buck when searching through archive data. This phase is also what is called Open Source Intelligence (OSINT).

Passive reconnaissance and active reconnaissance are the two primary forms of reconnaissance. For the first part of information gathering, you will focus on passive recon. Active recon will be completed in the fingerprinting/scanning phase.
Passive recon is crucial when investigating a target. This is where you will gather as much intelligence as possible to complete a successful penetration test. During this process, you will not interact directly with the target machine. No activities are logged or traced back to the you since all information gathered is already.
Example Tools Used for Passive Recon
Target validation – ICANN Lookup, nslookup, dnsrecon
Finding Subdomains – Google Fu, dig, nmap, Sublist3r, Bluto, crt.sh, assetfinder
Fingerprinting – wappalyzer, WhatWeb, BuiltWith, Netcat
DataBreaches – HavelBeenPwned, Breach-Parse, WeLeakInfo
- Maltego
- AMASS
- Bluto
- Breach-Parse
- Censys
- CMSMap
- DNSDumpster
Fingerprinting and Scanning
Bottom Line Up Front: Active reconnaissance
The fingerprinting and scanning phase, also known as the active recon phase, is where you will use the information gathered from the passive recon and dig deeper to know your target. This is why the passive recon stage is important because it will lay out a strong foundation to work with.

In this phase you will actively focus on engaging the target to detect specific open ports, web pages, network architecture, subnets, services, weaknesses, and provide you with a path on ways to potentially exploit them. Questions to be asked should include which ports are open? What operating systems? What software?
Example Tools Used for Active Recon
Active reconnaissance
- Nmap
- Wireshark
- Wireless antennas (e.g., Atheros AR9271, Ralink RT3070, Ralink RT3572)
- Aircrack-NG
- Kismet
- TCPdump
Vulnerability Assessment
Bottom Line Up Front: Discover & Research Vulnerabilities
After passive and active recon is completed, the vulnerability assessment phase will begin. In this phase, you will begin to actively discover vulnerabilities on what was discovered in the previous phases to determine how successful their exploit strategy could potentially be.

Vulnerability assessment is a methodical approach used to validate the existence of the vulnerability. This phase will be completed using both manual and automated assessment tools to validate if a vulnerability can be exploited.
Example Manual Assessment:
- CVEMITRE research
- CWE
- CAPEC
- ATT&CK
- Searchsploit
- Company website
Example Automated assessment:
- Tenable Nessus scan
- NMAP
- Metasploit Scanner Modules
- Nikto
Exploitation
Bottom Line Up Front: Use all intelligence gathered to exploit target.
The majority of a penetration test will be in the reconnaissance phases of an assessment. In the exploit phase, you will focus on running exploits against the vulnerabilities found. If you do the hard work up front with gathering as much information as possible, the exploitation phase will give you the flexibility to be creative with the attacks and how you pivot because you will have all the knowledge on the targets architecture.

Example Manual Exploitation:
- Manual custom scripts
- Ettercap (DNS Spoofing)
- Ettercap (Cache Poisoning)
- Ettercap (Arp Poisoning)
- Responder (LLMNR, NBT-NS, MDNS Poisoning)
- CEWL
- Crunch
- Hydra
- John the ripper
Example Automated Exploitation:
- Metasploit framework
Pivoting
- Are we able to pivot from one system to another?
- Are we able to escalate our privileges?
- Are we able to access another network?
Post Exploitation (Reporting)
Bottom Line Up Front: Post-report delivery activities
Report Writing
The final penetration testing report should be formal and impersonal. It should not directly target specific employees such as “your Windows administrator is doing a bad job securing the domain controller.”. The report needs to be explaining your findings in a technical and non-technical concept that is phrased in a way that is clearly explaining the finding and how it was exploited. Essentially, senior management who have no experience in security should be able to understand what is going on and the technical staff can also dig deeper in the report to see the technical findings. No sensitive information should be used and all screenshots containing sensitive information should be masked out.

Ultimately, the final pentest report will be an important artifact for the client to use, allowing senior management to make informed risk based decisions to mitigate any findings. The main guidlines in a report include:
- Executive Summary: Includes high-level summary of the pentest scope.
- Statement of Scope: Defines what was actually tested.
- Statement of Methodology: Describes the techniques used to execute the pentest.
- Statement of Limitation: Documents restrictions (e.g., time) imposed on the pentest.
- Testing Narrative: Elaborates on the outcome of the techniques used during testing.
- Segmentation Testing Results: Summarizes the testing of segmentation.
- Findings: Lists exploited vulnerability, target(s) affected, risk/severity rating, etc.
- Tools Used: Shows what tools aided the tester(s) with conducting the pentest.
- Cleaning Up the Environment: Provide direction on how information cleanup was performed.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.

