SUIDs and GUIDs | Understanding File Permissions for Linux and Best Practices for Secure Access Control
We’re a hub for tech professionals looking to advance & optimize their IT Infrastructure by finding the perfect product, tool, or role. Learn more about us. If you don’t see a product you are looking for on our website you can send us feedback 🙂

SUIDs and GUIDs are important components of file permissions in Unix-like operating systems. Understanding what they are and how they work is important for anyone who works with Unix-like operating systems. In this article, we will discuss what SUIDs and GUIDs are, how they work, and best practices for using them.
What are Permissions?
Before we dive into SUIDs and GUIDs, it’s important to understand what permissions are. In Unix-like operating systems, permissions control who can access files and directories, and what they can do with them. There are three types of permissions: read, write, and execute. Read permission allows a user to view the contents of a file or directory, write permission allows a user to modify the contents of a file or directory, and execute permission allows a user to run a file or access a directory.
Permissions are assigned to files and directories using a set of flags that determine who can access them and what actions they can perform. These flags are known as file modes.
What is SUID?
SUID (Set User ID) is a special file mode that allows a user to execute a file with the permissions of the file’s owner, rather than their own permissions. When a file with the SUID bit set is executed, it runs with the permissions of the user who owns the file, rather than the user who executed the file.
SUID is often used for programs that need to access system resources that are only accessible to certain users. For example, the ‘passwd’ command is often set to SUID so that users can change their own passwords, even if they don’t have write access to the password file.
- /bin/passwd – The ‘passwd’ command is often set to SUID so that users can change their own passwords, even if they don’t have write access to the password file.
- /usr/bin/su – The ‘su’ command is often set to SUID so that users can switch to another user account, even if they don’t have the password for that account.
- /usr/bin/ping – The ‘ping’ command is often set to SUID so that users can test network connectivity, which requires privileged access to network resources.
- /usr/bin/newgrp – The ‘newgrp’ command is often set to SUID so that users can switch to another group, even if they are not a member of that group.
- /usr/sbin/useradd – The ‘useradd’ command is often set to SUID so that users can create new user accounts, which requires privileged access to system resources.
What is GUID?
GUID (Set Group ID) is similar to SUID, but instead of running a file with the permissions of the file’s owner, it runs with the permissions of the file’s group. When a file with the GUID bit set is executed, it runs with the permissions of the group that owns the file, rather than the user who executed the file.
GUID is often used for programs that need to access system resources that are only accessible to certain groups. For example, the ‘sudo’ command is often set to GUID so that members of the ‘sudo’ group can run commands with root privileges.
- /usr/bin/sudo – The ‘sudo’ command is often set to GUID so that members of the ‘sudo’ group can run commands with root privileges.
- /usr/bin/passwd – The ‘passwd’ command can also be set to GUID so that members of the ‘shadow’ group can change passwords.
- /usr/bin/crontab – The ‘crontab’ command is often set to GUID so that members of the ‘cron’ group can schedule tasks to run automatically.
- /usr/bin/at – The ‘at’ command is often set to GUID so that members of the ‘at’ group can schedule one-time tasks to run at a specified time.
- /usr/bin/screen – The ‘screen’ command can also be set to GUID so that members of the ‘screen’ group can use the ‘screen’ utility to manage multiple terminal sessions.
Differences between SUID and GUID
While SUID and GUID are similar in that they allow a file to be executed with different permissions than the user who executed the file, there are some key differences between the two.
One of the main differences is that SUID runs with the permissions of the file’s owner, while GUID runs with the permissions of the file’s group. This means that SUID can be used to give a single user access to certain resources, while GUID can be used to give a group of users access to certain resources.
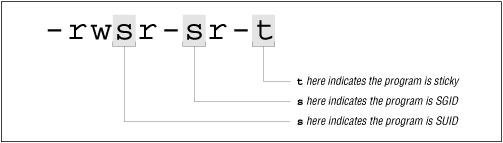
Another difference is that SUID is more commonly used than GUID. This is because SUID is often used for programs that need to access system resources that are only accessible to certain users, while GUID is used for programs that need to access system resources that are only accessible to certain groups.
Security Concerns and Best Practices
While SUID and GUID can be useful for providing access to system resources, they also pose security risks if not used properly. One of the main risks is that if a file with SUID or GUID is compromised, an attacker can gain access to system resources that they should not have access to.
To mitigate these risks, there are several best practices for using SUID and GUID:
- Use SUID and GUID sparingly: SUID and GUID should only be used for programs that need to access system resources that are only accessible to certain users or groups. Use them sparingly and only when necessary.
- Use the latest version of the software: Using the latest version of the software can help reduce the risk of security vulnerabilities.
- Use a non-default user or group: When setting SUID or GUID, use a non-default user or group to reduce the risk of attackers gaining access to system resources.
- Use auditing tools: Auditing tools can help identify files with SUID and GUID set, and can also help identify changes to files with SUID and GUID set.
- Use file system protections: File system protections, such as file permissions and access control lists, can help limit the ability of attackers to compromise files with SUID and GUID set.
Conclusion
In conclusion, SUID and GUID are important components of file permissions in Unix-like operating systems. Understanding what they are, how they work, and best practices for using them is important for anyone who works with Unix-like operating systems. While they can be useful for providing access to system resources, they also pose security risks if not used properly. By using them sparingly, using the latest version of the software, using a non-default user or group, using auditing tools, and using file system protections, users can reduce the risk of security vulnerabilities and ensure a secure and productive system.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.

